December 29, 2005
Chapell Associates
Chapell Associates is a consult firm on privacy and data collection. Chapell & Associates is headed by Alan Chapell. In 1997, Mr. Chapell founded the privacy program at Jupiter Research, an Internet research firm focusing on the consumer Internet economy. During his 4-1/2 years at Jupiter, Mr. Chapell also directed Jupiter's marketing, sales and compliance operations.
Services:
Compliance Services: Risk Assessment - Development of Privacy and Data Disclosure Policies - Implementation and Training - Data Warehousing and Database Design
Consumer Research
and
(and I think this is the most interesting)
Privacy Marketing - Research has demonstrated that the development of a robust privacy program creates significant opportunities. Organizations leverage privacy as a way to build customer trust, to support the collection of better customer data, and to market more effectively. Good privacy practices can lead to new revenue sources, particularly for organizations that posses, or seek to posses a well-known and respected brand. We develop privacy practices that increase ROI.
They have their own blog: http://www.chapellassociates.com/blog.htm
And papers and articles by Chapell & Scarborough
And Mr. Chapell will be the next guest at KUCI (Privacy Piracy) Next Wednesday (January 4th)
Publicado por
Carlos Garea
los
4:17 AM
1 comentarios
![]()
December 28, 2005
Privacy Piracy

KUCI is my favorite radio station. KUCI is brought to you by the University of California, Irvine
And there is program Privacy Piracy:
Every WEDNESDAY afternoon from 5-6 PM LIVE, Pacific Time on 88.9 FM in Irvine and WORLDWIDE live audio streaming at www.kuci.org
Privacy Piracy is a program by Mari Frank, who is attorney and privacy consultant, is the creator of The Identity Theft Survival Kit, the audiocassette series Identity Theft Prevention and Survival, co-author of Privacy Piracy.
In her website you can listen interviews with a lot of privacy gurus: Ponemon, Solove, Sullivan, Colleman.
This is our radio ¡¡ ¡ ¡
Publicado por
Carlos Garea
los
5:07 AM
0
comentarios
![]()
December 27, 2005
European Parliament approves communications data retention

Privacy International analyzes the Directive on communications data retention
" The European Parliament voted today to adopt a new directive allowing for the retention of data "generated by telephony, SMS and internet, but not the content of the information communicated". This data includes email addresses and location data from cell phones. The directive is highly controversial due to the impact it will have on the privacy of European Union citizens.
Also of concern is the broad discretion that is left to EU member states. For example, data may be accessed for the purposes of combatting serious crime and terrorism, but no concrete definition of these concepts has been provided, allowing member states to transpose their own definitions on the provisions of the Directive. In addition, the length of time that a telecommunications company has to retain the data is left relatively undefined - from a minimum of 6 months to a maximum of 24 months - and member states may extend these time frames. Already several countries have indicated intentions to. "
Full report at Privacy International.
LINKS:
Privacy International Data Retention
Data Retention Petition Campaign
Data Retention Directive
European Parliament
Publicado por
Carlos Garea
los
7:43 AM
0
comentarios
![]()
December 26, 2005
USA Patriot Act
 Spy powers: Extending, improving Patriot Act is the right goal
Spy powers: Extending, improving Patriot Act is the right goal
A Lansing State Journal editorial
"Congress has roughly another month to thoughtfully debate the USA Patriot Act; what it should keep to bolster the nation's security, and those provisions it should discard because they are a threat to civil liberties.
Late last week Congress agreed to extend the act until Feb. 3, and the White House has reluctantly agreed to the extension.
This temporary extension is a reasonable alternative to President Bush's preference: enshrining the entire act permanently in federal law.
Republican congressional leaders fought hard for the president's position, but an unlikely coalition of senators amassed a filibuster attempt, and Republican leaders relented. Now, perhaps, there can be a full and needed airing of the Patriot Act's strengths and weaknesses.
Earlier last week, the White House said it had prevented Senate Democrats from "killing the Patriot Act." That's inaccurate on at least two counts."
(Full editorial at Lansing State Journal)
Links:
EPIC:
Congress Enacts One-Month Patriot Act ExtensionFollowing widespread public debate, intense negotiation, and political maneuvering, the Congress has extended the Patriot Act until February 3, 2006. More information about the Patriot Act can be found at EPIC's FISA page, Patriot Act page, Patriot Act Sunset page, and Patriot Act FOIA page. (Dec. 23)
Daily Herald: In our View: Continue reviews of Patriot Act
El Diario (New York): Spying and the Patriot Act
Publicado por
Carlos Garea
los
3:15 AM
0
comentarios
![]()
December 24, 2005
Merry Xmas Joyeux Nöel Feliz Navidad
Merry Xmas ¡ ¡ ¡ ¡
Publicado por
Carlos Garea
los
2:28 AM
0
comentarios
![]()
December 16, 2005
Czech Republic

Czech Republic
Status of implementation of Directive 95/46 on the Protection of Individuals with regard to the Processing of Personal Data:
Consolidated version of the Personal Data Protection Act Act 101 of April 4, 2000 on the Protection of Personal Data and on Amendment to Some Acts.
Sensitive data in general
Position No. 2/2001 – The processing of trade-union membership sensitive personal data, October 2001
Position No. 5/2004 – The amount of paid trade-union dues as an income tax deductible, May 2004
Health data
Position No. 1/2000 – Medical records on patients, December 2000
Position No. 1/2002 – Personal data processing in the context of health care provision, August 2002
Position No. 3/2004 – Personal data processing in the context of clinical testing of drugs, January 2004
Administration and public registers
Position No. 4/2004 – Interpretation of application of a part of the Register of Population Act (on birth numbers), July 2004
Position No. 2/2004 – The access to personal data from municipal and regional bodies agenda, January 2004
Household & social activities, consumer rights
Position No. 2/2002 – Personal data processing in connection with library work, August 2002
Position No. 1/2004 – Identity checks at the entrance of a building, January 2004
Position No. 6/2004 – Copying of identity papers in the light of the PDP Act, November 2004
Credit reporting, finance and insurance
Position No. 1/2001 – Publication of the names of debtors, April 2001
Position No. 1/2005 – Activities of insurance intermediaries and the notification/registration obligation, May 2005
LINKS:
www.uoou.cz
Publicado por
Carlos Garea
los
2:43 AM
0
comentarios
![]()
December 15, 2005
Belgium

Today we begin a special editon of Policy Papers on Data Protection in Europe, the first one:
Belgium
Administration and public registers
Avis N°42/1997 Diffusion des décisions juridictionnelles par le recours aux technologies de l'information et de la communication, 23.12.1997
Household & social activities, consumer rights
Avis N°9/2005 sur un encadrement des listes noires, 15.06.2005
Credit reporting, finance and insurance
Note : les droits des personnes fichées à la centrale des crédits aux particuliers de la Banque Nationale (B.N.B.), 31.08.2003
Direct marketing
Note : marketing direct et protection des données personnelles, 24.03.2003
Avis N°34/2000 d'initiative relatif à la protection de la vie privée dans le cadre du commerce électronique, 22.11.2000
Telephone directories
Recommandation N° 01/1999 Utilisation des données conntenues dans les annuaires téléphoniques, 23.06.1999
Video surveillance
Avis d'initiative N°34/1999 relatif aux traitements d'images effectués en particulier par le biais de systèmes de vidéo-surveillance, 13.12.1999
LINKS:
Commission de la protection de la vie privée
Rue Haute, 139
B - 1000 BRUXELLES
Tel 32/2/542.72.00 Fax. 32/2/542.72.01 or 542.72.12
e-mail: commission@privacy.fgov.be
website
Research:
Facultés universitaires Notre-Dame de la Paix
CRID (Centre de Recherches Informatique et Droit)
Katholieke Universiteit Leuven
Interdisciplinary Centre for Law & Information Technology (ICRI)
Vrije Universiteit Brussel
Center for LAW, SCIENCE,TECHNOLOGY & SOCIETY STUDIES
Publicado por
Carlos Garea
los
8:02 AM
0
comentarios
![]()
December 14, 2005
Economic Evaluation of the Data Protection Directive

This report Economic Evaluation of the Data Protection Directive 95/46/EC, has been commissioned by the European Commission, Internal Market Directorate-General and prepared by RAMBOLL Management. The objective of this report is to measure the economic impact of the Directive on data controllers and to examine its cost effectiveness and efficiency by assessing the implementation and transposition process and analysing the direct costs of the directive.
"The case studies show that the costs of compliance with the national legislation implementing the Directive are limited for the sectors examined. Most companies, except the multinational companies (CSC and Benetton Italy) and large public institutions (customs authorities), experience modest costs. In addition the costs on multinational companies and large administrations are minor related to the size and turnover of these organisations."
Publicado por
Carlos Garea
los
7:42 AM
0
comentarios
![]()
December 13, 2005
Touch-screen voting machines
 Image Source: Diebold website www.diebold.com
Image Source: Diebold website www.diebold.com
The Beacon Journal writes about touch-screen voting machines, a device manufactured by Diebold Inc.
"Voters have told election officials they are concerned others can see the choices being made on new touch-screen voting machines.
The privacy concerns about the machines in wide use across the United States can be resolved with common sense approaches like careful placement of the machines, the manufacturer and Ohio's top election official said Monday"
Full article at: The Beacon Journal
ABOUT Diebold, Incorporated is a global leader in providing integrated self-service delivery systems and services. Founded in 1859, the company employs more than 14,000 associates with representation in nearly 90 countries worldwide and headquarters in Canton, Ohio, USA. Diebold reported revenue of US$2.4 billion in 2004 and is publicly traded on the New York Stock Exchange under the symbol 'DBD.'
Publicado por
Carlos Garea
los
8:58 AM
0
comentarios
![]()
December 12, 2005
Worker Privacy: You Have None
 Photo by artyfarty at Flickr.com
Photo by artyfarty at Flickr.com
Wired publishs this article by Joanna Glasner Worker Privacy: You Have None
"If you have internet access at work, there's a very good chance your employer has a system in place to monitor your online activities.
So, if you're concerned about privacy, take heed. Under current U.S. law, there's little you can do to protect the confidentiality of your internet use on the job. Here's a rundown of the rights you don't have at work.
Notice of monitoring: Only two states (Connecticut and Delaware) require that employers inform workers if they are monitoring online activity, according to Jeremy Gruber, legal director, the National Workrights Institute. Federal legislation requiring such disclosure has been proposed but not enacted.
That said, most employers do provide notice to employees if they track workplace web use. In an employer survey conducted this year by the American Management Association and the ePolicy Institute, 89 percent of respondents said they notify employees if their web usage is being tracked.
Privacy outside the office: More workers are telecommuting these days, often using laptops and other portable devices provided by their employer. But leaving the office doesn't guarantee freedom from internet surveillance..."
Full article at Wired.com
Publicado por
Carlos Garea
los
6:33 AM
0
comentarios
![]()
December 09, 2005
Privacy Enhanced Linking

There is a new publication by Latanya Sweeney
Privacy-Enhanced Linking
Citation: L. Sweeney. Privacy-Enhanced Linking. Accepted December 2005. Earlier version available as Carnegie Mellon University, School of Computer Science Technical Report CMU-ISRI-05-136. Pittsburgh: November 2005. (PDF)
Abstract
While computer scientists are uniquely situated to incorporate privacy protections in the link analysis algorithms they construct, most computer scientists are unaware of this opportunity and of ways to think about achieving needed protections. The work presented in this writing introduces a new way for computer scientists to think about providing privacy protection within link analysis and introduces the notion of “privacy-enhanced linking” as algorithms that perform link analysis with guarantees of privacy protection modeled after the Fair Information Practices. In this approach, privacy protection is realized by assessing the validity and interpretation of link analysis results such that inappropriate harm to individuals is provably minimized.
Publicado por
Carlos Garea
los
4:59 AM
0
comentarios
![]()
December 07, 2005
Building Trust
In general, trust refers to an aspect of a relationship between two parties, by which a given situation is mutually understood, and commitments are made toward actions in favor of a desired outcome. In contrast with hope, trust is almost strictly interpersonal. In contrast with faith, trust is almost always considered a subordinate material form whereas "faith" is typically reserved for a "higher power" — God, etc.
The term trust also has other meanings in several different fields:
Contents
1 Sociology
2 Property law
3 Economic history
4 Finance
5 Computer science
6 Music
This book: Building Trust: How to Get It! How to Keep It! by Hyler Bracey, explain how to build it.
Publicado por
Carlos Garea
los
8:33 AM
0
comentarios
![]()
December 05, 2005
Xbox 360 & Privacy
 Voila this is the new Xbox 360 by Microsoft. And as you can play online you have to be carefoul with your privacy.
Voila this is the new Xbox 360 by Microsoft. And as you can play online you have to be carefoul with your privacy.
Two websites where you can read more about it:
Gamespot:
"Privacy is always a concern when you're online, but the Xbox 360 lets you specify a variety of settings to make sure you only interact with the people you want to interact with."
Hexus.gaming:
"Now no doubt Microsoft has this totally covered in its Terms and Conditions that you have to agree to when you sign up for an Xbox LIVE account, but did you know just how much information Microsoft shares with other Xbox 360 owners about what you’re doing? Simply put, anyone you’ve been in contact with through Xbox LIVE can subsequently see what you’re up to, regardless of whether they’re in your friends list or not. "
Full article at: Hexus.gaming
Publicado por
Carlos Garea
los
7:25 AM
0
comentarios
![]()
December 03, 2005
The Face Book
From the Social Software Weblog
Thefacebook.com, which resembles the website Friendster, enables users to upload photographs, personal information and their course lists. Members can create networks by looking up other users and inviting them to be friends.
After a friendship is confirmed, users are electronically linked to each other from their profile pages. The website also allows users to graphically visualize how their friends are connected in an intricate web.
...Teaching Assistant in Germanic Languages and Literatures Geraldine A. Grimm, one of the teachers who signed up for the website, said much of the faculty is prejudiced against the site… “After checking out the site, I was impressed by the all-inclusive nature of a Friendster-style Harvard site that brings undergrads, grads, alums, faculty and staff together,” she wrote.
From the mac weekly
Privacy issues confront the rapidly expanding collegiate online networkBrian MartucciStaff Writer
Launched in February 2004 by three Harvard roommates (who dropped out of school to run the site after it became popular), Facebook was '"initially a small project that we imagined Harvard students would enjoy,"' a company spokesperson said in the British newspaper The Guardian. "[It] really works as an information directory and not just as a site you go to when you're bored or need entertainment."
Full article at The Mac Weekly
Publicado por
Carlos Garea
los
3:11 AM
0
comentarios
![]()
December 02, 2005
Venky Shankar
Venkatesh (Venky) Shankar is Professor of Marketing and Coleman Chair in Marketing at the Mays Business School, Texas A&M University. He was a visiting scholar at the Sloan School of Management, MIT. His areas of specialization include Digital Business, Competitive Strategy, International Marketing, Pricing, Retailing, New Product Development, and Biotechnology.
He has different papers about Trust & Privacy:
Online Trust: A Stakeholder Perspective, Concepts, Implications, and Future Directions
Price Levels and Price Dispersion on the Internet
Publicado por
Carlos Garea
los
5:40 AM
0
comentarios
![]()
November 30, 2005
November 29, 2005
Consumer Privacy: A free choice approach

The Pacific Research Institute (PRI) is a free-market think tank providing practical solutions for the issues that affect the daily lives of all individuals. Since its founding in 1979, PRI has remained steadfast to the vision of a free and civil society where individuals can achieve their full potential.
And there is available this study "Consumer Privacy A Free Choice Approach" by Sonia Arrison who is the director of the Center for Freedom and Technology (CFT) at the California-based Pacific Research Institute.
Este Estudio está disponible para Consumidores de habla Española, "Privacidad del Consumidor: Un Enfoque de Libre Elección", destaca las tecnologías que pueden utilizar para proteger la privacidad.
Publicado por
Carlos Garea
los
7:55 AM
0
comentarios
![]()
November 28, 2005
CIO Insight

I think it is the first time I visit CIOinsight.com web site, and never it is too late. It is a great magazine, great columns:
The Value of Trust Through Privacy By Edward Cone September 15, 2004
The Value of Trust Through Privacy
Introduction
Privacy And Profits
Performance Indicator
Core Privacy Values
Details Matter
Making Privacy Work
The Ultimate Privacy Argument Against RFID By Evan Schuman, Ziff Davis Internet October 21, 2005
Petition Demands Privacy for Electronic Health Records By M.L. Baker, Ziff Davis Internet October 28, 2005
Publicado por
Carlos Garea
los
8:47 AM
0
comentarios
![]()
November 25, 2005
Lack of privacy affects productivity
The Indian Express publishes this article by Amy Joyce.
Cubicle misery: Lack of privacy affects productivity
Nosy colleagues and irritating chats curb an individual’s efficiency, locked doors can perhaps solve the problem
" Do you remember those days when you could slip into your private office, close the door and make that personal phone call? Or escape from maddening co-workers? Or simply have some quiet time to read that academic paper you needed to check out?
With at least 70 per cent of office workers spending their days in cubicles or open offices without any sort of dividers, very few workplaces have doors and, therefore, privacy anymore. Which means many workers have workplace complaints that involve burnt popcorn, speaker phones and lurkers/starers. Because without the walls workers used to have, we all have to share much more personal aspects of our lives than ever before." .....
Full article at The Indian Express
Publicado por
Carlos Garea
los
4:11 AM
0
comentarios
![]()
November 24, 2005
Video Surveillance
 Image by XCaballe from Flickr:http://www.flickr.com/photos/xcaballe/18943611/
Image by XCaballe from Flickr:http://www.flickr.com/photos/xcaballe/18943611/
Souriez vous êtes filmés" est depuis 1995 un collectif de personnes désireuses de ne pas sombrer dans une société de technologie répressive et de proposer des alternatives militantes festives. L’association s’est donnée comme but le retrait des caméras de vidéo-surveillance, elle entend être un lieu de regroupement humain pour débattre de la société dans laquelle nous souhaitons vivre. Son combat politique et culturel est pluriel, elle oeuvre avec des associations comme AC ou comme le RATP (réseau pour l’abolition des transports payants) http://ratp.samizdat.net/ et organise des actions (masquage de caméras) parfois à l’échelle internationale avec des groupes comme le SCP newyork http://www.notbored.org.
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
The Observing Surveillance Project documents the presence of video cameras placed in Washington DC after September 11. The project was undertaken by the staff of the Electronic Privacy Information Center (EPIC) in Washington, DC. Many of the images displayed in the exhibit may be viewed online at www.observingsurveillance.org.
Publicado por
Carlos Garea
los
7:16 AM
0
comentarios
![]()
November 23, 2005
EPIC: Spotlight on Surveillance
 Image source: http://www.identix.com/
Image source: http://www.identix.com/
EPIC (Electronic Privacy Information Center) publishes this month, a report about Facial Recognition Systems Have an Ugly Effect on Personal Privacy.
"The federal government is spending an increasing amount of money on surveillance technology and programs at the expense of other projects. EPIC's "Spotlight on Surveillance" project scrutinizes these surveillance programs. For more information, see previous Spotlights on Surveillance.1
This month, Spotlight focuses upon the government’s use of facial recognition systems.2 The Departments of State, Energy, Justice and Defense have spent at least $47 million on such systems.3 In Fiscal Year 2006, the federal government plans to add facial recognition checks to all visa applications, which already include fingerprint biometrics.4 This is despite the Government Accountability Office’s estimate that incorporating biometric systems into visas would cost from $1.3 billion to $2.9 billion for startup, and $700 million to $1.5 billion for annual operating costs.5 Federal funds have been used by cities and states to buy facial recognition devices for motor vehicle and police departments.6 New U.S. passports and national identification cards created under the REAL ID Act of 2005 will both include digital photographs that can be linked to facial recognition systems.7 However, several tests, including those conducted by the National Institute for Standards and Technology (NIST) and the Department of Defense, show that facial recognition systems can be easily befuddled by uncooperative subjects and changes in the environment, such as positioning or lighting.8 Such facial recognition systems create significant privacy risks because the technique is surreptitious, the prospects for extensive profiling are clear, and there are no laws that currently regulate these systems to prevent abuse. "
Full report at Epic.org
Publicado por
Carlos Garea
los
7:25 AM
0
comentarios
![]()
November 21, 2005
Sony & DRM
Where was Sony's Privacy Officer?
November 21, 2005 By Ray Everett-Church
As this month's controversy over Sony's distribution of music CDs with flawed digital rights management (DRM) software continues to play itself out, the whole mess is already primed to become a classic case study in why corporations need competent Privacy Officers to keep them out of trouble.
According to news reports, about 20 different CD titles issued in recent months by Sony's BMG music distribution group have been outfitted with software called eXtended Copy Protection (XCP). Designed to thwart illegal copying of music files, more than two million CDs containing XCP were shipped, mainly to retailers in the United States.
If you're like tens of millions of music lovers around the world, you often use your computer as your CD player, choosing to manage your music through software like Apple's iTunes or Yahoo's Musicmatch.
Full article at: Earthweb.com
Links:
Texas Versus Sony BMG Security Pronews
Sony BMG sued over CD spyware Hollywood Reporter
Texas sues Sony BMG over CDs
Patch issued for Sony CD uninstaller CNET News.com
Texas sues Sony BMG for spyware violations Reuters
Sony BMG Sued Under Anti-Spyware Laws ABC News
Publicado por
Carlos Garea
los
11:35 PM
0
comentarios
![]()
November 18, 2005
Symposium on Search Engines, Law, and Public Policy
The Information Society Project (ISP) at Yale Law School was created in 1997 to study the implications of the Internet, telecommunications, and the new information technologies on law and society.
At ISP will take place next December 3, 2005 a "Symposium on Search Engines, Law, and Public Policy",
"Search is big business, and search functionality increasingly shapes the information society. Yet how the law treats search is still up for grabs, and with it, the power to dominate the next generation of the online world. How will this potential to wield control affect search engine companies, their advertisers, their users, or the information they index? What will search engines look like in the future, and what is the role of regulators in this emerging market? This symposium will map out the terrain of search engine law & policy.
Regulating Search? is the first academic conference devoted to search engines and the law. The symposium will bring together technologists, policymakers, entrepreneurs, executives, lawyers, computer scientists, and activists to discuss the emerging field of search engine law. It will examine trends in litigation involving search engines, identify the interests that are implicated by the increasing legal control of search, and discuss appropriate public policy responses."
Publicado por
Carlos Garea
los
2:49 AM
0
comentarios
![]()
November 17, 2005
Privacy by Bearing Point

BearingPoint provides strategic consulting, application services, technology solutions and managed services to Global 2000 companies and government organizations.
One of these services is Security Systems Integration, and Privacy Services for Information Resources.
" Today’s market leaders leverage the Internet to increase market share and profitability. Because of the prevalence of online business-to-consumer, businessto- business, and consumer-to-consumer activities, your organization must institutionalize the privacy of electronic business information exchange to protect your most important asset and that of your customers—information.
At BearingPoint, we can help you implement the proper controls to advance your online business model and avoid making costly privacy mistakes. As part of our larger Security solutions suite, our Privacy Services offer an enterprise-wide integration approach that can help your company reduce costs, increase accuracy, enhance customer trust and satisfaction, and gain a competitive advantage through improved customer service and information security."
There is a PDF available "PROTECT VALUABLE DATA RESOURCES FOR COMPETITIVE ADVANTAGE".
By the way, BearingPoint has a magazine Business Empowewed, and the last number issue 3, 205 there is a article very interesting about Retailers;
The 21st Century Retailer by Harry King, about the future enterprise and Customer-centric enterprise, customer loyalty and two fantastic quotes:
“A retailer must win the heart of today’s savvy customer by asking, ‘What’s unique about my merchandise and service?’” he says.
“In other words, what will differentiate them in the eyes of their customer? That’s what it’s all about.”
Could be privacy ?
Publicado por
Carlos Garea
los
3:33 AM
1 comentarios
![]()
November 16, 2005
RFID & Privacy: OECD Forum, Paris, 5 Oct 2005
Last October, OECD, hold a forum on RFID & Privacy, presentations are available;
1. WELCOMING REMARKS AND INTRODUCTION BY THE CHAIR [9:30 – 9:40]
Hugo Parr, Director General, Ministry of Modernisation, Norway, and Chair of OECD Committee for Information, Computer and Communications Policy - Presentation
2. DESCRIPTION OF RFID TECHNOLOGY AND ITS POTENTIAL [9:40 TO 11:00]
Introductory remarks and session moderator: Jonathan Collins, European Editor for RFID Journal
2.1. Panorama of RFID current applications and potential economic benefits [9:40 – 10:10]
Dan Caprio, Deputy Assistant Secretary for Technology Policy and Chief Privacy Officer, U.S. Department of Commerce - Presentation
Naji Najjar, Director of Wireless Broadband & Sensing Solutions, IBM Southwest Europe - Presentation
2.2. Future applications, ubiquity of RFID and potential economic and social benefits [10:10 – 11:00]
Taiichi Inoue, Senior Consultant - Head of IT for Society Consulting Group, Nomura Research Institute, Ltd. - Presentation
Indro Mukerjee, Executive vice president, Automotive & Identification business unit, Philips Semiconductors - Presentation
Elliot Maxwell, Fellow of the Communications Program at Johns Hopkins University - Presentation
3. COSTS/BENEFITS IN DIFFERENT TYPES OF APPLICATIONS [11:30 – 12:30]
Introductory remarks and session moderator: Richard Rees, President, Scanology Group, and Chair British Standards Institution Technical Committee “Automatic Identification Techniques” - Presentation
3.1. Smart tags along the supply chain [11:30-12:00]
Claudia Loebbecke, Professor, University of Cologne - Presentation
Masakazu Fujita, Research Director, Next Generation Electronic Commerce Council of Japan (ECOM) - Presentation - Appendix
3.2. Smart tags at the item-level and smart cards in service applications [12:00 – 12:30]
Elie Simon, Chief Executive Officer, TAGSYS SA - Presentation
Mark MacCarthy, Senior Vice President for Public Policy, VISA USA - Presentation
RFID DEMONSTRATIONS IN ROOM 1 [13:15 – 14:15]
IBM Demonstration: RFID in supply-chain management applications
Philips and VISA demonstration: payment applications with contactless pay cards and RFID-enabled mobile phone - Presentation
4. CRITICAL ISSUES FOR POLICY MAKERS [14:15 – 17:00]
4.1. Infrastructure/standards panel discussion [14:15 – 15:30]
Introductory remarks and session moderator: Dave Wollman, Scientific Advisor and RFID Coordinator, National Institute of Standards and Technology (USA)
Henri Barthel, Technical Director EPCglobal, GS1 - Presentation
Simson Garfinkel, Postdoctoral Fellow, Center for Research on Computation at Society at Harvard University - Presentation
Kyo-il Chung, Director, ETRI (Electronics and Telecommunications Research Institute, Korea) - Presentation
Bernard Benhamou, Senior Lecturer, Political Science Institute, Paris - Speech
4.2. Privacy panel discussion [15:45 – 17:00]
Introductory remarks and session moderator: Joseph Alhadeff, Vice President for Global Public Policy and Chief Privacy Officer, Oracle Corporation
Marc Rotenberg, Executive Director, Electronic Privacy Information Center - Presentation
Florent Frederix, Scientific Officer for RFID, European Commission Infosoc D-G - Presentation
Stephania Congia, International Department of the Italian Data Protection Commission - Presentation
Jeroen Terstegge, Corporate Privacy Officer, Philips, and Member of the EICTA (Chair) and ICC Privacy and RFID Working Groups - Presentation
5. ROUNDTABLE DISCUSSION & CONCLUSION [17:00 – 18:00]
Chaired by Hugo Parr, Director General, Ministry of Modernisation, Norway, and Chair of OECD Committee for Information, Computer and Communications Policy
5.1 Summary of important elements from the Forum [17:00 – 17:20]
Peter Ferguson, Director, Electronic Commerce Branch, Industry Canada
Richard Foggie, Assistant Director, Electronics and IT Services, DTI
Tony Taylor, European director, EPCGlobal Inc.
Jeremy Ward, Director of Service Development, Symantec EMEA
5.3 Open discussion of important elements from the Forum [17:20 – 17:50]5.4 Overall summary and next steps [17:50 – 18:00 ]
5.4 Overall summary by Hugo Parr, Director General, Ministry of Modernisation, Norway, and Chair of OECD Committee for Information, Computer and Communications Policy
Potential future work by the OECD: next steps
Publicado por
Carlos Garea
los
3:50 AM
3
comentarios
![]()
November 15, 2005
Eurobarometers on privacy
 Picture from: RTD Info magazine Nov 2005
Picture from: RTD Info magazine Nov 2005
RTF Info is a magazine by European Commission on European Research.
Last number, november 2005, is dedicated to two surveys: Europeans, Science and Technology and Social values, Science and Technology .
One of these questions was privacy:
" Privacy and freedom of expression
Protecting information about our private life from misuse and exploitation - Protecting freedom of speech and information. A very large majority of Europeans are concerned about the need for this dual protection. Almost 70% regard it as “very important” and over a quarter as “fairly important”.
The protection of private life, in particular with the increasing traffic in virtual information, is thus a matter of concern to citizens, reflecting their interest in a subject that is laid down in Article 8 of the Charter of European Fundamental Rights. The application of this right constitutes a very clear challenge in a society where information obtained by those engaged in electronic commerce, insurance, health care and many other private spheres of activity is stored in databanks. Not only are these insufficiently protected against possible piracy but their very use by the operators in question can raise ethical questions due to the growing intrusion into an individual’s private life.
The Czechs (81%), the Greeks (78%) and the British (77%) prioritise the importance of protecting personal data – as do the Icelandics (83%) and the Norwegians (81%) outside the EU. A similar unanimity is found for freedom of speech and information, also laid down in the Charter of European Fundamental Rights: 95% of Europeans attach importance to this (including the 68% who regard it as “very important”). A similar degree of unanimity is found throughout the various socio-cultural strata. However, in the ‘new’ EU states there is a tendency maybe to view the importance of the application of these rights in more relative terms. "
Publicado por
Carlos Garea
los
3:56 AM
0
comentarios
![]()
November 14, 2005
Sperm-donor, DNA & Privacy
 Image Source : http://www.wisniewskis.de
Image Source : http://www.wisniewskis.de
Last week, New Scientist, published this article “Anonymous sperm donor traced on internet”, how a 15-year-old boy who was conceived using donor sperm discovered his genetic father.
“The teenager tracked down his father from his Y chromosome. The Y is passed from father to son virtually unchanged, like a surname. The Y is passed from father to son virtually unchanged, like a surname. So the pattern of gene variants it carries can help identify which paternal line an individual has descended from and can also be linked to a man's surname.The boy paid FamilyTreeDNA.com $289 for the service”
“Using another online service, Omnitrace.com, he purchased the names of everyone that had been born in the same place on the same day.”
Publicado por
Carlos Garea
los
4:46 AM
0
comentarios
![]()
November 11, 2005
Trusted Pear

Primum Group Technologies (PGT) announced plans to present its new privacy and anonymity technology in Albany,New York during the week-long National Small Business Innovation Research(SBIR)/Small Business Technology Transfer (STTR) Conference from 14-18November. PGT are developers of a new web-based technology -- "TrustedPear(TM)" -- so named because it provides trusted exchange between pairs ofexchange partners.
Publicado por
Carlos Garea
los
3:19 AM
0
comentarios
![]()
November 10, 2005
HBR articles about privacy
Harvard Business Review published last december an article about Privacy & Technology by Roberta A. Fusaro, for read this article, you must pay it online or go to a library and read the Harvard Business Review number Dec 2004.
"Tracking technologies--in products and services like TiVo and electronic toll collection--make people's lives a lot more convenient. But the public is understandably concerned about the privacy issues such technologies raise. No one is more aware of those issues than Dante Sorella, CEO of Raydar Electronics, which develops and sells radio frequency identification (RFID) tags and readers"
But I have found this article in spanish for free: www.infobaeprofesional.com
Privacidad y tecnología. Como Gran Hermano
"Ante una oferta para utilizar etiquetas de identificación en un bien de consumo, un ejecutivo se pregunta: ¿se ofrece un servicio valioso al cliente o se invade su vida? Las tecnologías de seguimiento como la RFID han hecho más transparentes que nunca las vidas de las personas"
Publicado por
Carlos Garea
los
2:37 AM
0
comentarios
![]()
November 09, 2005
3M: Electronic Vehicle Registration
 Image source 3M
Image source 3M
Electronic Vehicle Registration (EVR) is a product by 3M that uses Radio Frequency Identification technology to electronically identify vehicles and validate the identity, status, and authenticity of vehicle data. This enables government agencies to automatically detect and screen vehicles for compliance with federal, state, and municipal vehicle regulations.
- Automatically detects and screens vehicles for compliance with federal, state, and municipal vehicle regulations
- Automated enforcement actions and violation processing for non-compliant vehicles
- Increases effectiveness and efficiency of current government processes
There are videos in English, Spanish and Portuguese availables.
And this Brochure.
Publicado por
Carlos Garea
los
4:15 AM
0
comentarios
![]()
November 08, 2005
Ambient Agoras

Despite it is over Ambient Agoras it was a European Project Developed between 2001 – 2003.
" This Project amazing project, aims at providing situated services, place-relevant information, and feeling of the place (‘genius loci’) to users, so that they feel at home in the office.
In our approach, we are combining two perspectives that can be taken towards the issue of how the computer will disappear. We propose that disappearance can happen in two ways: via the “physical disappearance” by becoming very small due to miniaturization; via the “mental disappearance” of devices by becoming "invisible" because they are integrated/embedded in the physical environment (e.g., walls, doors, tables) around us. "
Privacy Issues
"The “Disappearing Computer (DC)” approach raises some fear among users because of the increased possibilities of being observed and of loosing control over private information, due to hidden functionality based on embedded invisible devices. This fear is certainly not entirely irrational, and the potential of DC indeed enables invasive capture of private data. On the other hand, as DC is devoted to collaborating with the user and supporting him, it needs to know things about the user. How can this be achieved without the user being put in embarrassing situations where personal data are disclosed to the wrong person, or used by others against his will? As privacy is a cultural notion, it may vary in time and space. The limit between privacy and isolation is not easy to define; as the right to be left alone competes with the right to be informed. To cover all these issues, we will provide a general framework for privacy design."
Download the European Disappearing Computer Privacy Design Guidelines (Version 1, November 2003, pdf-file, 190KB)
Facing the privacy issues: Privacy Guidelines for DC (organized by Saadi Lahlou, Laboratory of Design for Cognition, EDF R&D, Paris, François Jegou, Dalt Brussels & Politecnico di Milano Marc Langheinrich, ETH Zürich) (Download the "Open Day"-Schedule, pdf-file)
Project Partners:
The Integrated Publication and Information Systems Institute (IPSI) of the German Fraunhofer Gesellschaft (FhG) in Darmstadt, serves as the scientific and technical as well as the administrative coordinator of the project. It has expertise in developing innovative concepts and software prototypes in the fields of human-computer interaction, CSCW, and hypermedia environments. The research division AMBIENTE - »Workspaces of the Future« will contribute based on its earlier work in the areas of meeting rooms, Roomware®, and Cooperative Buildings.
EDF (Electricité de France) , the French electrical power utility, is the user organisation in the consortium. The Laboratory of Design for Cognition (LDC), located near Paris, of its R&D division develops and evaluates a wide range of office environments. In the project, it contributes innovative observation and evaluation methods as well as participative design techniques. Their K1-Building will provide a versatile testbed for the project.
Wilkhahn, located in Bad Münder (Germany), develops design-oriented, high quality products and interior concepts for applications in high quality segments, e.g., creating innovative office environments. Together with its design company "wiege" (Wilkhahn Entwicklungs GmbH), they provide the expertise for designing and building the planned artefacts. They will make use of their specific experience gained in the design of the second generation of Roomware® components developed in cooperation with IPSI as part of the Future Office Dynamics Consortium.
More about Ambient Intelligence:
OCW AmI Course: MAS. 963 and MAS.961
AMIGO Project (Ambient Intelligence for the Networked Home Environment)
Publicado por
Carlos Garea
los
5:07 AM
0
comentarios
![]()
November 07, 2005
Patient Privacy Rights

Image Source Patient Privacy Rights' Website
Article from EPIC NEWS
On October 26th, EPIC joined with Patient Privacy Rights in an effort to establish stronger protections in the United States for patients' medical information.
"2005 is the year that the American public learned that massive security breaches of personal information have made identity theft the number one crime in America. We must not allow the most sensitive personal records that exist, our medical records, to go online without adequate privacy safeguards," said EPIC Executive Director Marc Rotenberg.
Congress is rushing to pass legislation to establish a national Health Information Network without patient privacy protections. Yet recent surveys show that Americans consider the privacy of medical records to be a major concern. A Harris poll this past February found that 69 percent of adults do not believe strong enough data security will be installed in the system. An earlier Gallup survey found that 78 percent of the American public feel it is very important that their medical records be kept confidential. And the Markle Foundation found that more than three out of four respondents (79%) supported the right for a patient to control who can access his health information.
"No one should be able to see or use your medical records without your permission," said Dr. Deborah Peel, founder and chairman of the Patient Privacy Rights Foundation. "Americans must have confidence in the privacy and security of their online medical records."
As part of the effort to protect patients' privacy rights, the two groups are circulating an online petition calling for strong medical privacy safeguards.
The petition states simply:
-- I want to decide who can see and use my medical records
-- I do not want my medical records or those of my family's to be seen or used by my employer
-- I should never be forced to give up my right to privacy in order to get medical treatment.
Patient Privacy Rights is an Austin, Texas-based national consumer organization devoted to medical privacy.
"I Want My Medical Privacy!" petition:
http://www.patientprivacyrights.org/petition
Patient Privacy Rights site:
http://patientprivacyrights.org
Publicado por
Carlos Garea
los
7:33 AM
0
comentarios
![]()
November 04, 2005
FIDIS (Future of Identity in the Information Society)

FIDIS (Future of Identity in the Information Society) is a NoE (Network of Excellence) supported by the European Union under the 6th Framework Programme for Research and Technological Development within the Information Society Technologies (IST) priority in the Action Line: “Towards a global dependability and security framework”.
FIDIS work is structured into 7 research activities:
1. “Identity of Identity”
2. Profiling
3. Interoperability of IDs and ID management systems
4. Forensic Implications
5. De-Identification
6. HighTech ID
7. Mobility and Identity
The FIDIS consortium consists of the following partners:
1. Goethe University Frankfurt
Germany
2. Joint Research Centre (JRC)
Spain
3. Vrije Universiteit Brussel
Belgium
4. Unabhängiges Landeszentrum für Datenschutz
Germany
5. Institut Europeen D’Administration Des Affaires (INSEAD)
France
6. University of Reading
United Kingdom
7. Katholieke Universiteit Leuven
Belgium
8. Tilburg University
Netherlands
9. Karlstads University
Sweden
10. Technische Universität Berlin
Germany
11. Technische Universität Dresden
Germany
12. Albert-Ludwig-University Freiburg
Germany
13. Masarykova universita v Brne
Czech Republic
14. VaF Bratislava
Slovakia
15. London School of Economics and Political Science
United Kingdom
16. Budapest University of Technology and Economics (ISTRI)
Hungary
17. IBM Research GmbH
Switzerland
18. Institut de recherche criminelle de la Gendarmerie Nationale
France
19. Netherlands Forensic Institute
Netherlands
20. Virtual Identity and Privacy Research Center
Switzerland
21. Europäisches Microsoft Innovations Center GmbH
Germany
22. Institute of Communication and Computer Systems (ICCS)
Greece
23. AXSionics AG
Switzerland
24. SIRRIX AG Security Technologies
Germany
Publicado por
Carlos Garea
los
5:08 AM
1 comentarios
![]()
November 02, 2005
Google, ads and privacy
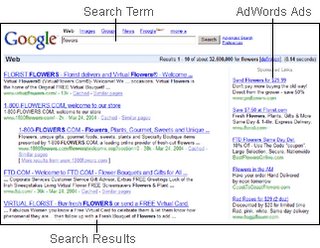
Last sunday, The New York Times publised this article Google Wants to Dominate Madison Avenue, Too by SAUL HANSELL
"Google already sells its text ads for many other sites on the Internet (including nytimes.com), and is also moving tentatively to sell the picture-based interactive advertising preferred by marketers who want to promote brands rather than immediately sell products. Now it is preparing to extend its technology to nearly every other medium, most significantly television. It is looking toward a world of digital cable boxes and Internet-delivered television that will allow it to show commercials tailored for each viewer, as it does now for each Web page it displays."
And this blog by Jack Schofield from Guardian Unlimited, Google, advertising, and the future of privacy
" The scary bit is that Google can target ads better if it knows more about you. And if it knows everything you have ever seached for on Google, knows who your friends are (Orkut), has read all your email (Gmail) and instant messages and listened to your phone calls (Google Talk) then it may well know far about you than your parents, your spouse or your boss."....
"Of course, Google doesn't tie all your personal information together in a Big Brother-style database, yet. But if Google doesn't, then Yahoo or Microsoft MSN or some new service almost certainly will. At the moment, Google says it only uses location information (ZIP codes)"
Publicado por
Carlos Garea
los
1:44 AM
0
comentarios
![]()
October 31, 2005
New Internet Identification in Korea to Protect Privacy

Image source: Ministry of Information and Communication Republic of Korea
New Internet Identification to Protect Privacy
From Digital Chosun Ilbo (English Edition)
Korea is adopting a new identification system for website access from 2007 to protect users' privacy. Those who want to join a website will no longer register with their real name and resident registration number, but will use a personal identification number (PIN) assigned by a credit-rating agency or certified authentication institute.
The Ministry of Information and Communication said Monday it settled on five identification methods to guard against theft of personal information after a series of high-profile crimes where hackers obtained access to users online banking accounts. The methods include three via credit-rating agencies and two via certified authentication institutes; the ministry wants online firms to adopt more than one of them. " If lawmakers pass the Personal Information Protection Act next year, major web portals and online game providers will have to adopt an alternative to resident registration numbers from 2007",ministry official Lee Seong-ok said.
Links:
Is privacy cure worse than the disease? Some say yesJoongang Ilbo, South Korea
Foolproof ID to Be Adopted for Online Registration Korea Times
Korea to introduce new ID system for internet services Korea Herald
On the Net, your history lingers Joongang Ilbo
Publicado por
Carlos Garea
los
7:37 AM
0
comentarios
![]()
October 28, 2005
SWAMI (AmI & Privacy)
SWAMI (Safeguards in a World of Ambient Intelligence) is a FP6 Project (European R&D Research Programme). This project aims to identify and analyse the social, economic, legal, technological and ethical issues related to identity, privacy and security in the forecasted but not yet deployed Ambient Intelligence (AmI) environment.
WORK PACKAGE
Work package 1 (WP1) consists of a state of the art review of existing AmI projects, studies, scenarios and roadmaps.
Work package 2 (WP2) deals with developing "dark" (adverse) scenarios, the aim of which will be to expose key socio-economic, legal, technological and ethical risks and vulnerabilities related to issues such as identity, privacy and security.
Work package 3 (WP3) develops legal and policy options which could serve as safeguards and privacy-enhancing mechanisms for Ambient Intelligence.
Work package 4 (WP4) focusses on dissimination of project results, continuously throughout the project. There are two validation and awareness-raising workshops foreseen. A final conference at the end of the project is also planned.
SWAMI Partners:
Fraunhofer Institute Systems and Innovation Research (Germany)
Institute for Prospective Technological Studies, DG-JRC, European Commission (Spain)
Vrije Universiteit Brussel (Belgium)
Technical Research Centre of Finland , VTT Electronics (Finland)
Trilateral Research & Consulting (UK)
There is available this report: The brave new world of ambient intelligence: A state-of-the-art review.
Links:
About Ambient Intelligence (Open Course Ware MIT) Course available
Philips Research: Ambient Intelligence
Publicado por
Carlos Garea
los
4:13 AM
3
comentarios
![]()
October 27, 2005
theBiometrix
Few days ago, we talked about the new european biometrics web site, Europeanbiometrics.info, and there is another Forum: The Biometrix
TheBIOMETRIX.COM was founded in mid January 2005 by a group of enthusiastic researchers & web developers from the UK, USA, Romania, Greece & Morocco.
The forum is easy to use and has numerous helpful features for free, once you have registered you can check the FAQ section, where you can find answers for your questions and how theBIOMETRIX.com forum functions.
Publicado por
Carlos Garea
los
7:20 AM
0
comentarios
![]()
October 26, 2005
US Passports and RFID
All U.S. passports will be implanted with computer chips starting next October, the State Department said Tuesday.
Links:
SFGates
Silicon.com
InformationWeek
RFID Journal
ABC News
Publicado por
Carlos Garea
los
7:26 AM
0
comentarios
![]()
October 25, 2005
What European Consumer think about RFID

Capgemini, one of the world's foremost providers of Consulting, Technology and Outsourcing services, published Capgemini in February 2005, this report RFID and Consumers: What European Consumers Think About RFID and the Implications for Business.
" European consumers are beginning to recognise that Radio Frequency Identification (RFID) technology will bring real benefits to their everyday lives, reveals new research from Capgemini. The majority of respondents said they would buy RFID-enabled products if they meant potentially reducing car theft (70% of those surveyed), faster recovery of stolen items (68%) and improved security of prescription drugs (63%). Additional benefits of RFID identified as important to consumers include improved food safety and quality; faster, more reliable notification of recalls; and faster exit through store checkouts.
However, the study also found that concerns over privacy issues threaten to overshadow the benefits of RFID. More than half (55%) of those surveyed are either concerned or very concerned that RFID tags will allow businesses to track consumers via product purchases, while 59% are worried that RFID tags will allow data to be used more freely by third parties. " (Source Cap Gemini)
Publicado por
Carlos Garea
los
8:39 AM
0
comentarios
![]()
October 24, 2005
Privacy in the Digital Networked Economy
Publicado por
Carlos Garea
los
7:41 AM
0
comentarios
![]()
October 21, 2005
Virtual Identity and Privacy - VIP

VIP takes care of all the subjects that deal with Identity and Privacy. It stands between the Computer Science Department and the Mathematics Department.
VIP is a member of Fidis. FIDIS (Future of Identity in the Information Society) is a NoE (Network of Excellence) supported by the European Union under the 6th Framework Programme for Research and Technological Development within the Information Society Technologies (IST) priority in the Action Line: "Towards a global dependability and security framework".
VIP's website provides a lot of reports and brochures about privacy:
Special issue of TILT on the "Impact of new technologies on privacy and data protection". D.-O. Jaquet-Chiffelle is the editor of a special issue of TILT on the "Impact of new technologies on privacy and data protection".
Editorial(pdf: 127Ko)
Table of content(pdf: 62Ko)
Special Issue(pdf: 2.4Mo)
Publicado por
Carlos Garea
los
3:54 AM
0
comentarios
![]()
October 20, 2005
Spychips

Spychips: How Major Corporations and Government Plan to Track Your Every Move with RFID, is a new book by Katherine Albrecht and Liz McIntyre, that they are founders of CASPIAN (Consumers Against Supermarket Privacy Invasion and Numbering) Published at Thomas Nelson, Inc.
Publicado por
Carlos Garea
los
4:04 AM
0
comentarios
![]()
October 19, 2005
Privacy in Korea: PICO

Republic of Korea is one of the most fascinanting countries right now, As one of the four East Asian Tigers, South Korea has achieved an impressive record of growth and integration into the high-tech modern global economy, making South Korea the 10th largest economy in the world
Visit Korea.net: Gateway to Korea, available in french, english, spanish, german, arabic, japanese, chinese and vietnamese.
About Privacy, The Personal Information Dispute Mediation Committee(PIDMC) is an independent statutory body established on December 3, 2001 on the basis of the "Act on Promotion of Information and Communications Network Utilization and Information Protection, etc."
As the Internet and IT services are popularized recently, personal information is used as basic marketing data, and thus the commercial value of it is being highlighted. Accordingly, the excessive collection, abuse and misuse of personal information have become social problems
In order to cope with these challenges, PIDMC was established for a quick and convenient settlement at an affordable cost as one of the alternative dispute resolution(ADR) mechanisms in Korea.
And we can see, this major case:
Case where an online game company collected personal information of an 11-year-old minor without consent of legal guardian
The complainant is a parent whose 11-year-old son, an elementary school student, registered as a member to the online game site operated by the respondent, an online game company, and who learned that his son had used the fee-based game services and had been charged approximately KRW180,000 for the games.The complainant claimed that he had never consented to the collection of the personal and payment information by the respondent when his son had joined the website of the respondent, and demanded the secession of his sons membership and refund of the charged service fees from the respondent. PICO recommended immediate membership withdrawal, along with the refund of KRW 180,000.
Publicado por
Carlos Garea
los
2:32 AM
0
comentarios
![]()
October 18, 2005
Here come the printers¡¡¡¡¡¡¡¡¡
 Photo Source www.eff.org Electronic Frontier Foundation
Photo Source www.eff.org Electronic Frontier Foundation
Electronic Frontier Foundation has discovered that many printers add an arrangement of yellow dots to each page printed that can allow the authorities to identify the time and date of printing and serial number of the device.
List of Printers which do or don't print tracking dots
The U.S. Secret Service admitted that the tracking information is part of a deal struck with selected color laser printer manufacturers, ostensibly to identify counterfeiters. However, the nature of the private information encoded in each document was not previously known.
"We've found that the dots from at least one line of printers encode the date and time your document was printed, as well as the serial number of the printer," said EFF Staff Technologist Seth David Schoen.
Publicado por
Carlos Garea
los
3:44 AM
0
comentarios
![]()
October 17, 2005
Security Breach Survey
White & Case LLP is a global law firm that has lawyers in the United States, Latin America, Europe, the Middle East, Africa and Asia. White & Case showcases its leadership in privacy and data protection law with an annual survey and symposium, that we talked about it, few time ago, the 5th Annual Global Privacy Symposium.
Now, they release this Report "Security Breach Survey", conducted by Ponemon Institute (dedicated to advancing ethical information and privacy management practices in business and government) to learn how individuals individuals react to data security breach notifications sent by business, non-profit or governmental organizations as required by new laws.
Publicado por
Carlos Garea
los
5:53 AM
0
comentarios
![]()
October 14, 2005
Siemens: Horizons 2020
Siemens has released this project Horizons 2020
"Will the future be a golden age or an apocalypse? People have always speculated about life in the future. Siemens has begun to search for answers and, with a communications scenario called Horizons2020, to study what life will be like in the world of tomorrow. The result is a series of distinct and exciting visions of life in the year 2020. These visions challenge the imagination and invite us to reflect and think ahead."
Two scenarios:
Horizon I
Horizon II
Check out this topic "Security and Public health"
Security and health for all Satellite-supported and online warning systems allow for rapid response to security and public health risks. Read vision
Security according to your budget Security is a marketable commodity. The more money you have, the more secure you can be. Read vision
Publicado por
Carlos Garea
los
5:02 AM
2
comentarios
![]()
Privacy saved my life
Blog Archive
-
▼
2005
(211)
-
▼
December
(16)
- Happy new year ¡ ¡
- Chapell Associates
- Privacy Piracy
- European Parliament approves communications data r...
- USA Patriot Act
- Merry Xmas Joyeux Nöel Feliz Navidad
- Czech Republic
- Belgium
- Economic Evaluation of the Data Protection Directive
- Touch-screen voting machines
- Worker Privacy: You Have None
- Privacy Enhanced Linking
- Building Trust
- Xbox 360 & Privacy
- The Face Book
- Venky Shankar
-
►
November
(19)
- Happy Birthday ¡ ¡
- Consumer Privacy: A free choice approach
- CIO Insight
- Lack of privacy affects productivity
- Video Surveillance
- EPIC: Spotlight on Surveillance
- Sony & DRM
- Symposium on Search Engines, Law, and Public Policy
- Privacy by Bearing Point
- RFID & Privacy: OECD Forum, Paris, 5 Oct 2005
- Eurobarometers on privacy
- Sperm-donor, DNA & Privacy
- Trusted Pear
- HBR articles about privacy
- 3M: Electronic Vehicle Registration
- Ambient Agoras
- Patient Privacy Rights
- FIDIS (Future of Identity in the Information Society)
- Google, ads and privacy
-
►
October
(20)
- New Internet Identification in Korea to Protect Pr...
- SWAMI (AmI & Privacy)
- theBiometrix
- US Passports and RFID
- What European Consumer think about RFID
- Privacy in the Digital Networked Economy
- Virtual Identity and Privacy - VIP
- Spychips
- Privacy in Korea: PICO
- Here come the printers¡¡¡¡¡¡¡¡¡
- Security Breach Survey
- Siemens: Horizons 2020
-
▼
December
(16)
Labels
- 23 and me (2)
- add (1)
- ADVISE (1)
- amazon (1)
- anti-REAL ID (1)
- Arizona State University (1)
- Ars Electronica (1)
- Australia (1)
- Balkin (1)
- Beresford (1)
- Berkeley (3)
- big brother (1)
- BITE (1)
- blogs (1)
- Bluetooth (1)
- books (3)
- brain (1)
- Brand Channel (1)
- brand loyalty (1)
- Branding (1)
- business week (1)
- camera phone (1)
- Canada (2)
- Carnegie Mellon (1)
- CDT (1)
- celebrity (2)
- cell phone (1)
- Center for Embedded Networked Sensing (1)
- Christopher Kuner (1)
- Clinton (1)
- college (1)
- conference (1)
- Consumer Protection (2)
- Consumers (1)
- Copyright (1)
- cord blood bank (1)
- cordon umbilical (1)
- Customer Respect Group (1)
- Cybercrime (1)
- data mining (3)
- data protection (2)
- databases (1)
- deCode Genomics (1)
- digital information (1)
- DNA (1)
- DRM Technologies (1)
- drugs (1)
- e-Identity (1)
- e-Smart (1)
- EDPS (1)
- eema (1)
- emsense (1)
- encryption (1)
- ENISA (2)
- EPIC (3)
- Europe (2)
- European Biometric Forum (2)
- European Commission (8)
- European Law (1)
- European Parliament (2)
- European Privacy Institute (1)
- Facebook (2)
- FIDIS (1)
- freedom of expresion (1)
- Front Line Defenders (1)
- GAO (1)
- Gates (1)
- genome (2)
- George Duncan (1)
- google (4)
- HAAS (1)
- Harvard (2)
- health privacy (3)
- HHS (1)
- Hitachi (1)
- hospital (1)
- IBM (2)
- IBM Privacy Research Institute (1)
- id card (1)
- Identity (1)
- Institute for Information Law (1)
- Internet (6)
- Internet code of conduct (1)
- Internet Phone (1)
- IP address (1)
- Ireland (1)
- Italy (1)
- Japan Privacy (1)
- Knome (1)
- KPMG (1)
- library (1)
- location (3)
- Luc Wathieu (1)
- Lynn Upshaw (1)
- Marketing (3)
- McCain (1)
- microsoft (6)
- mobil (1)
- Move on (1)
- Mutanen (1)
- Navigenics (2)
- Obama (1)
- OCLC (1)
- Odlyzko (1)
- One Laptop per Child (1)
- Oxford Internet Institute (1)
- Paris Hilton (1)
- Passenger (1)
- Patient Privacy Rights (1)
- personal health records (2)
- PET (1)
- Phone (2)
- price discrimination (1)
- PRIME (1)
- privacy (3)
- privacy blogs (1)
- public sphere (1)
- Queen's University (1)
- Ralf Bendrath (1)
- RFID (6)
- RSA (1)
- SAITS (1)
- Scentric (1)
- Science (1)
- Sensors (1)
- Silicon Republic (1)
- Smart Card Alliance (1)
- social networks (7)
- Sociology (1)
- Spyblog (1)
- Stanford (2)
- Stockholm University (1)
- STS Civic Forum (1)
- Supernova (1)
- surveillance society (4)
- SWAMI (1)
- Sweden (1)
- TACD (1)
- Technology Review (9)
- telecom (1)
- Tivoli (1)
- TrustE (1)
- Ubiquitous Computing (2)
- UCLA (1)
- UK (2)
- umbilical cord blood (1)
- university (1)
- University of Reading (1)
- University of Texas (1)
- USA privacy (6)
- Valyd Software (1)
- video surveillance (1)
- vodafone (1)
- VTT (1)
- web 2.0 (2)
- Werbach (1)
- Wharton (1)
- wireless (2)
- yahoo (2)
- Yale Law University (1)
- Yourstreet (1)
- youtube (1)
European National Data Agencies
Links
- Data Privacy Lab Carnegie Mellon
- Berkeley Center for Law & Technology
- Centre de Recherches Informatique et Droit FUNDP, Namur
- Berkman Center for Internet & Society
- Institute for Pervasive Computing
- Tilburg Institute for Law, Technology and Society
- LEFIS Legal Framework for Information Sociecty
- EPIC Electronic Privacy Information Center
- EFE Electronic Frontier Foundation
- Stanford Center for Internet and Society
- Privacy International
- Privacy and Identity in the Information Society PRIDIS
- Data Protection - European Commission
- Interdisciplinary Centre for Law & ICT K.U.Leuven
- Privacy in Asia - University of Singapore
- IBM Privacy Research Institute
- Hp Labs: Trust, Privacy & Security
- Virginia Journal of Law & Technology
- Privacy Exchange
- Health Privacy Project
- OECD Information Security and Privacy
- Health Privacy Project
- Privacy Network Project
- DNA and Privacy Project
- privacidad
- privacy
Contact Me
- Carlos Garea
- carlosgarea@gmail.com